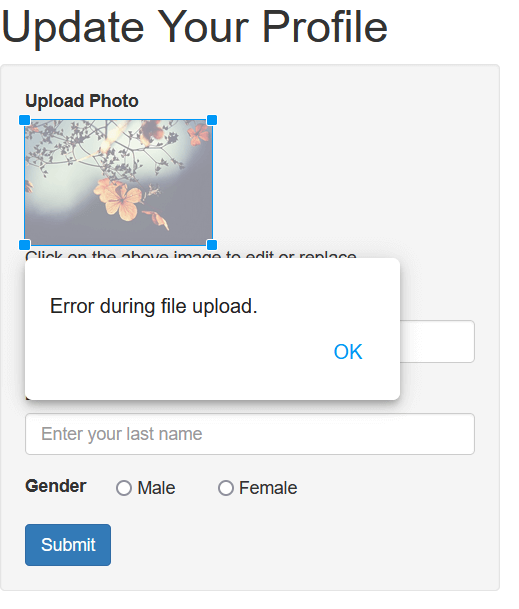
Ethical Hacking Prof. Indranil Sengupta Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur
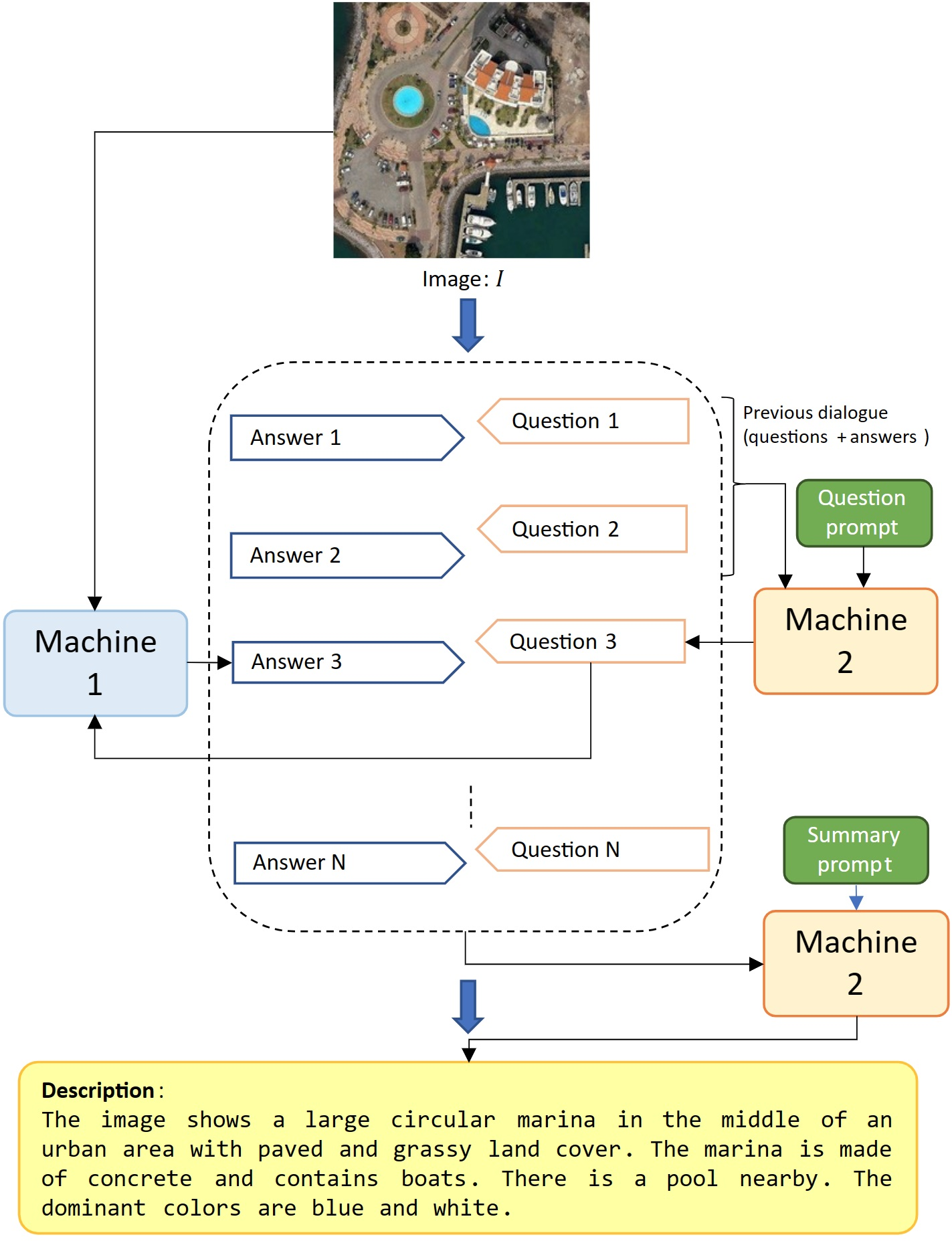
Remote Sensing | Free Full-Text | Machine-to-Machine Visual Dialoguing with ChatGPT for Enriched Textual Image Description

Development and evaluation of wireless 3D video conference system using decision tree and behavior network | EURASIP Journal on Wireless Communications and Networking | Full Text

Câmeras Online. É muito comum encontrarmos equipamentos… | by Marcos Henrique | 100security | Medium
Ethical Hacking Prof. Indranil Sengupta Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur

High-throughput detection and tracking of cells and intracellular spots in mother machine experiments | Nature Protocols
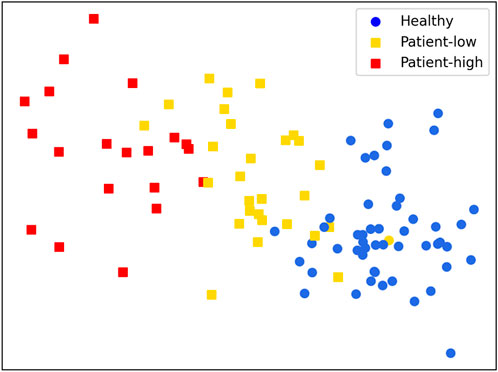
Frontiers | Effective evaluation of HGcnMLP method for markerless 3D pose estimation of musculoskeletal diseases patients based on smartphone monocular video
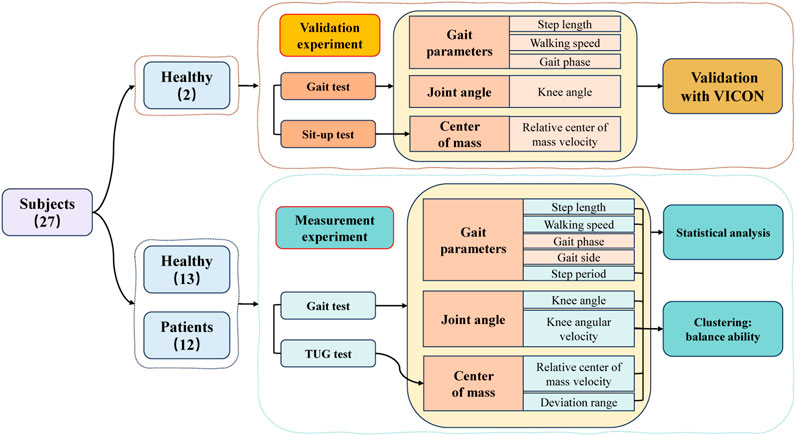
Frontiers | Effective evaluation of HGcnMLP method for markerless 3D pose estimation of musculoskeletal diseases patients based on smartphone monocular video
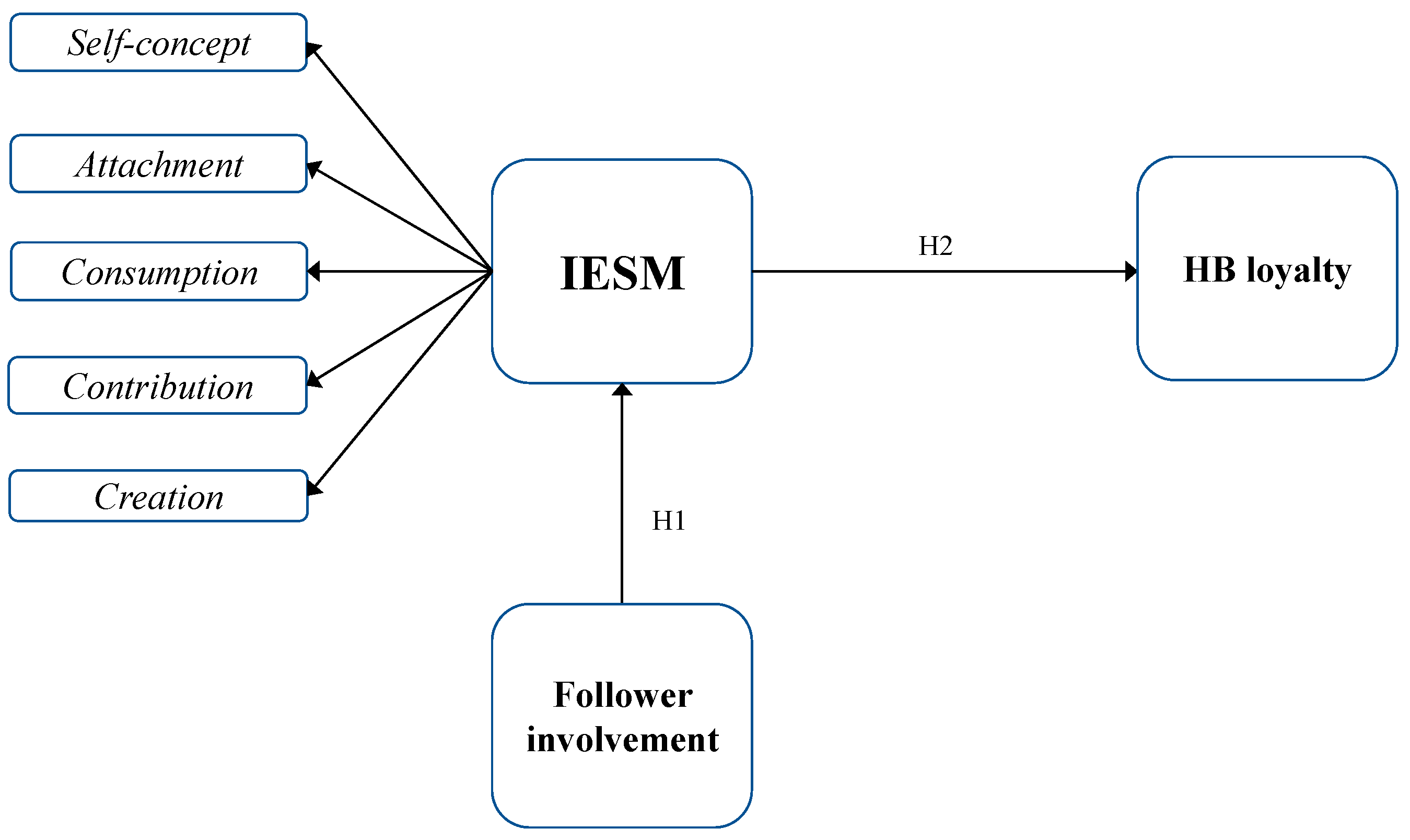
JTAER | Free Full-Text | Influencer Engagement on Social Media: A Conceptual Model, the Development and Validation of a Measurement Scale
Ethical Hacking Prof. Indranil Sengupta Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur

A system for extracting structural information from Social Network accounts - Buccafurri - 2015 - Software: Practice and Experience - Wiley Online Library

Application of human–computer interaction system based on machine learning algorithm in artistic visual communication | Soft Computing




![PDF] Security Technique using SSH Tunneling for CCTV Remote Access | Semantic Scholar PDF] Security Technique using SSH Tunneling for CCTV Remote Access | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/b0cd537d01f39ecb5e85403672b3a80857584e96/2-Table1-1.png)